Several Canadian carriers and their flanker brands include trackers from Google, Facebook and others in mobile apps offered to customers.
After recently switching to Telus, I downloaded the company’s mobile app to see if there were any features I wanted to use. Within a few hours of downloading the My Telus app, I noticed that DuckDuckGo’s App Tracking Protection had blocked almost 1,400 tracking attempts using known third-party trackers from Google, Facebook and Adobe.
App Tracking Protection, if you haven’t heard of it, is a feature offered in the DuckDuckGo mobile app for Android. The functionality has been around for almost a year (I first wrote about it early in 2022), but it recently entered public beta, meaning anyone with an Android phone can download the app and try it out. It uses a VPN to filter network traffic coming from your device and blocks known third-party trackers to prevent data from leaving your device. Even though it uses Android’s built-in VPN feature, DuckDuckGo says everything is handled on-device, and App Tracking Protection doesn’t route data through external servers. The search company even made the blocklist used for App Tracking Protection publicly available on GitHub.
Curious if Telus was an outlier, I downloaded the mobile apps offered by several Canadian carriers and wireless providers available in Ontario, including:
- My Telus
- MyRogers
- Fido My Account
- My Chatr
- MyBell
- Virgin Plus My Account
- Lucky Mobile
- Freedom My Account
It’s worth noting that Telus’ flanker brands Koodo and Public Mobile don’t offer mobile apps. Additionally, testing was performed on a Pixel 7 running Android 13 and the November 2022 security patch. The apps weren’t tested on iPhone since the iOS version of the DuckDuckGo app doesn’t support App Tracking Protection (iOS does offer built-in App Tracking Transparency, which I’ll touch on further down).
Trackers collect a variety of data
The trackers blocked by DuckDuckGo’s App Tracking Protection can collect a wide array of data. App Tracking Protection lists information that each tracker is known to collect, such as information about the device being used, such as screen resolution, network/carrier, OS version, charging status, device language, headphone status, system volume, rotation data, and more. The trackers also try to collect some personal data, including location, gender, postal code, and email. Trackers also collect unique identifiers, advertising IDs, GPS coordinates, available memory and storage, and much, much more.
The screenshots below show the trackers detected in Canadian carrier apps and what those trackers are known to collect:
Allison Goodman, a senior communications manager for DuckDuckGo, told MobileSyrup in an interview that apps may include these trackers for things like analytics and marketing, noting that over 96 percent of popular free Android apps tested by DuckDuckGo contain hidden third-party trackers. 87 percent sent data to Google, and 68 percent sent data to Facebook. DuckDuckGo also cited an AppCensus report with similar results.
“Personal data companies like Facebook and Google use that information to build a profile that advertisers and content-targeting companies use to influence what you see online,” Goodman wrote.
“The problems with all this information collection go way beyond so-called ‘relevant’ (aka creepy) advertising and targeting. Tracking networks can sell your data to other companies like data brokers, advertisers, and governments, resulting in more substantial harms like ideological manipulation, discrimination, personal price manipulation, polarization, and more.”
Trackers in carrier apps
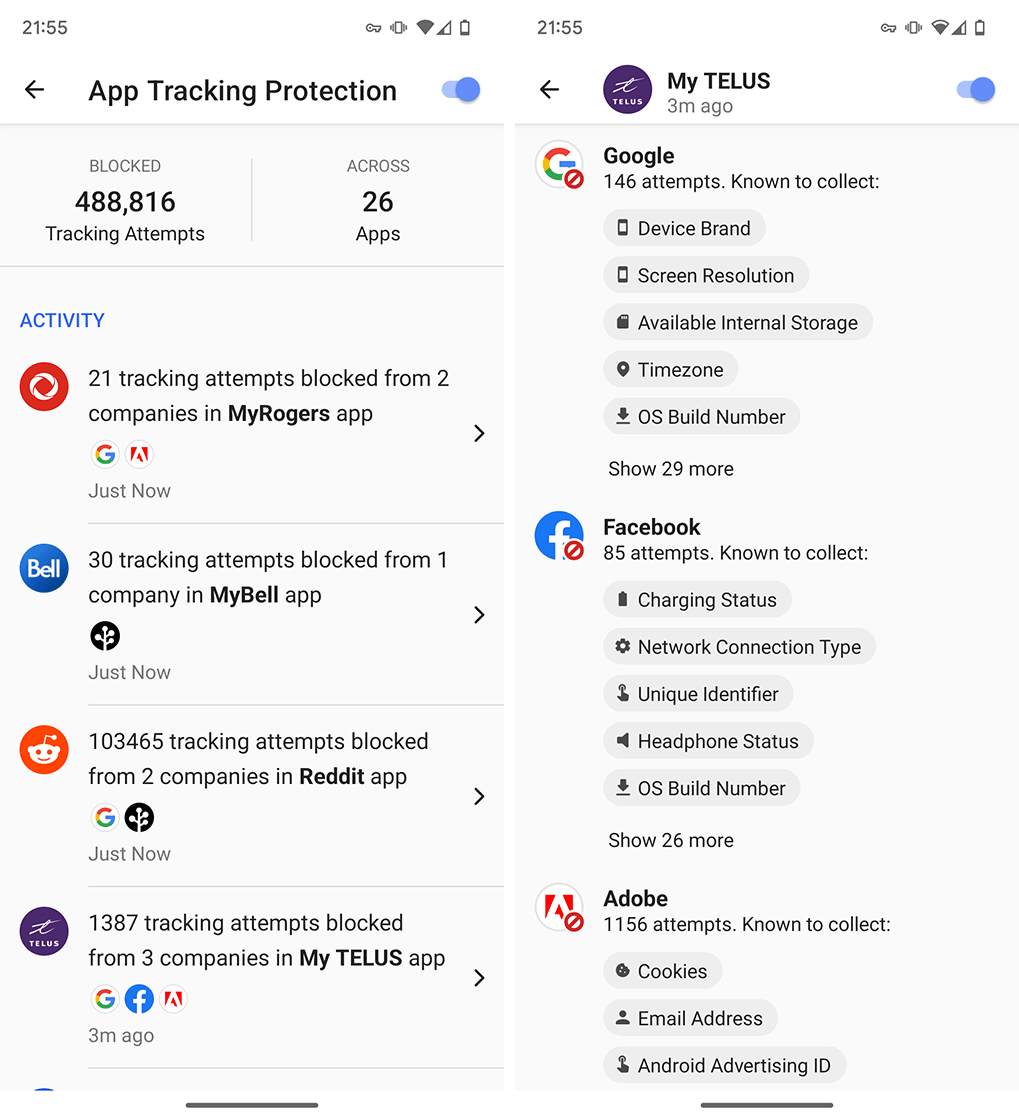
App Tracking Protection blocked Google, Facebook, and Adobe trackers in the My TELUS app.
The My Telus app racked up tracking attempts faster than apps from other providers and was also one of only two that included trackers from Facebook. The other was Freedom Mobile’s My Account app. My Telus also included Google and Adobe trackers.
Telus did not provide comment in time for publication.
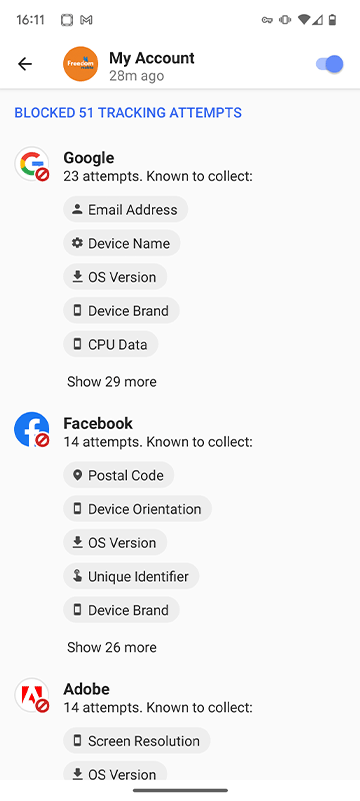
App Tracking Protection blocked Google, Facebook, and Adobe trackers in the Freedom app
Along with the Facebook trackers, App Tracking Protection blocked Google and Adobe trackers from Freedom Mobile’s app.
Freedom did not provide comment in time for publication.
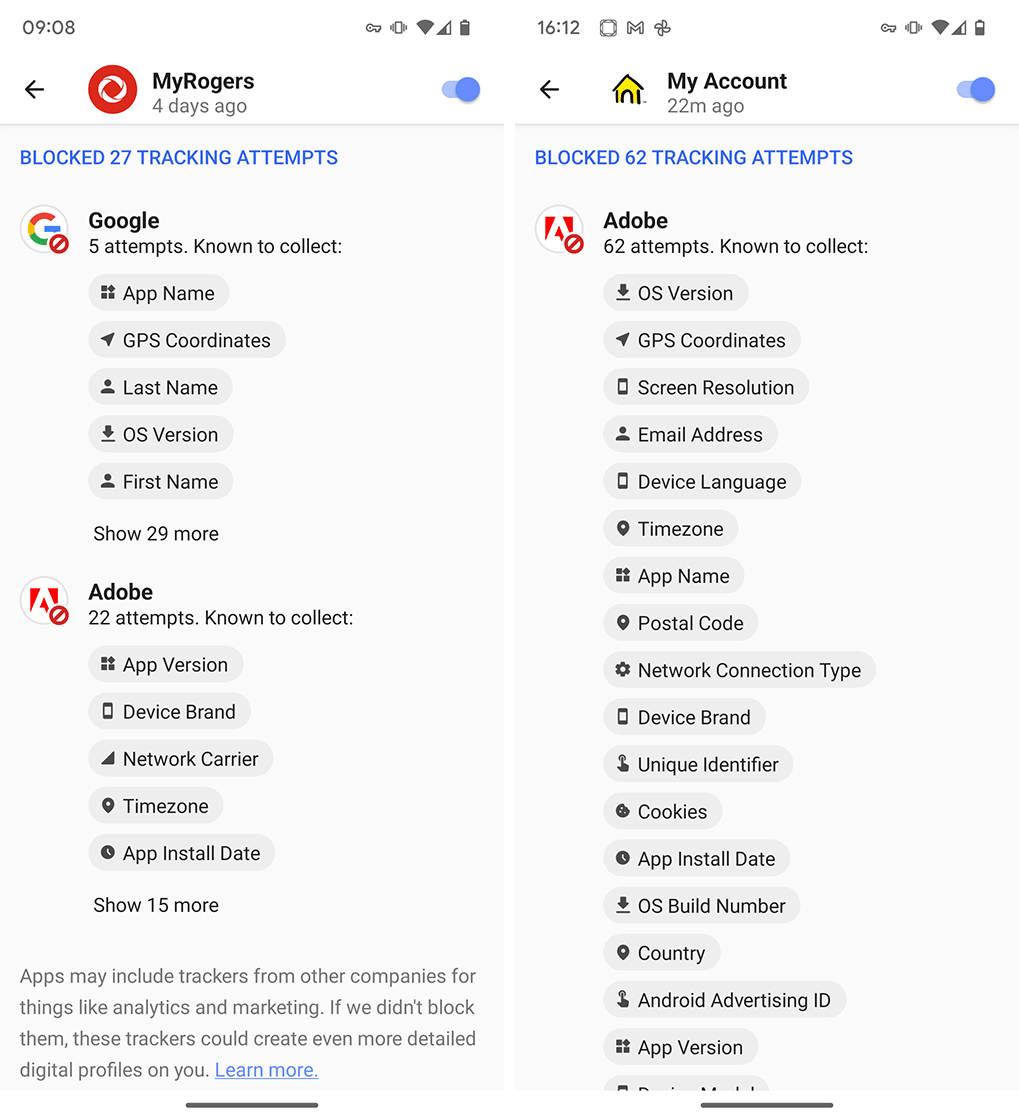
App Tracking Protection blocked Google and Adobe trackers in Rogers’ and Fido’s apps
Rogers, as well as flanker brand Fido, had both Google and Adobe trackers. Interestingly, App Tracking Protection blocked no trackers from the Chatr app.
A Rogers spokesperson told MobileSyrup that information collected by the MyRogers and Fido My Account apps is used for internal analytics and diagnostics to determine app functionality and operating system support. Moreover, the spokesperson said that the apps don’t disclose customer information with third parties for cross-tracking across apps and websites. Instead, all data is collected and used solely by Rogers and Fido. The Rogers spokesperson said that only customers can choose whether to enable location services and that doing so allows customers to receive more relevant information, like regional service offerings or details about regional network issues.
The spokesperson also emphasized that Rogers’ apps comply with all Canadian privacy laws, including PIPEDA, and both the Google and Apple developer policies.
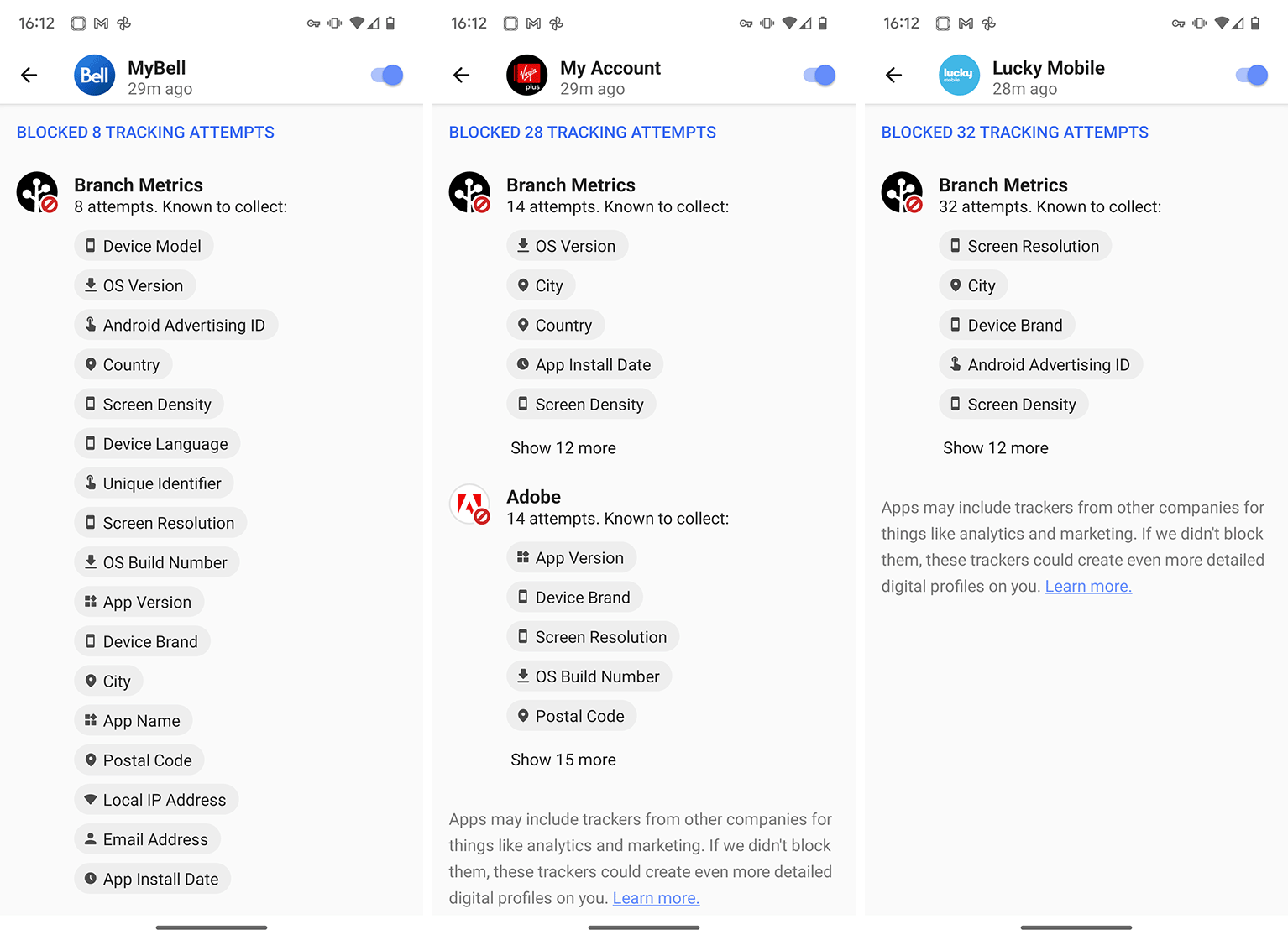
Bell app tracking attempts blocked by App Tracking Protection
Finally, the Bell, Virgin Plus, and Lucky Mobile apps all had trackers blocked by App Tracking Protection. For the most part, Bell and related apps used a third-party tracker from Branch Metrics. According to the Branch Metrics website, it “provides the leading mobile linking platform, with solutions that unify user experience and measurement across different devices, platforms, and channels,” which sounds a lot like analytics. Still, the App Tracking Protection detailed that Branch Metrics is known to collect data like location, email address, postal code, device details, local IP address, and more.
In a statement to MobileSyrup, Bell said:
“The MyBell, Virgin Plus MyAccount and Lucky Mobile apps are used by customers to manage their account and billing, check their usage as well as technical support. In order to provide these services to customers, we need certain information such as device platform, the version of the operating system, and IP address. We also know which province that the customer is located in, because our pricing and services are based by region. However, we do not collect location below the provincial level, nor do we request or use background location. Maintaining the privacy and security of our customers’ personal information is a priority for us, and we do not share this information with other parties.”
What about iPhone users?
As I mentioned above, DuckDuckGo’s iPhone app doesn’t offer App Tracking Protection, but iOS has a built-in App Tracking Transparency feature. However, it differs from App Tracking Protection by operating primarily on an agreement with app developers — if a user chooses to opt out of tracking for an app, then that app can’t use that user’s Identifier for Advertisers (IDFA). However, research revealed many apps build digital fingerprints on users by collecting other data, meaning App Tracking Transparency doesn’t actually do much to stop tracking (Moreover, Apple’s own apps don’t follow the setting).
MobileSyrup asked each carrier whether their apps respected the App Tracking Transparency feature included in iOS. Those that provided comment to MobileSyrup for this story did not directly answer the question, and only Rogers brought up Apple developer policies.
Ultimately, you may want to remove any carrier apps installed on your smartphone, especially if you have concerns about the tracking. Most carrier apps offer the same functionality as what’s available through carrier websites, so there isn’t really a need to install the apps anyway. Moreover, if your Android device comes with one of these apps pre-installed and you can’t remove it, head to Settings > Apps > See all apps > Select the carrier app > Tap ‘Disable.’ This is about as close to uninstalling a pre-installed app as you can get.
Alternatively, download DuckDuckGo’s app and enable App Tracking Protection. Honestly, you might want to do this anyway — it will block trackers from more than just carrier apps. The DuckDuckGo app is available for free on the Play Store.