Last week, I wrote about installing GrapheneOS, an open-source, Android-based privacy operating system, on a Pixel 3. I shared some initial impressions, but now I’m back after using the GrapheneOS Pixel 3 as my daily driver for a week.
As I said in my initial impressions, GrapheneOS offers a low bar for entry from a technical perspective thanks to a straightforward install process (if you follow the guide on their website).
Using GrapheneOS once it’s installed, however, isn’t quite at the “it just works” level. I think that’s something important to keep in mind for anyone interested in trying out GrapheneOS. To be clear, GrapheneOS works, and works quite well (more on that below). But it’s often not a seamless experience like using an unmodified Pixel or an iPhone.
I don’t blame GrapheneOS for this — it’s entirely Google’s fault. Android, in its current form, is a hodgepodge of open-source software and proprietary Google-made software. Often, the Google software forms the backbone of the modern Android experience most people are familiar with.
GrapheneOS is an excellent way to reveal how much of the Android experience is reliant on Google because it takes Google out of the equation entirely. That’s what surprised me the most in my week using GrapheneOS — there are so many things, both big and small, obvious and not so obvious, where Android relies in part (or whole) on Google software.
Google, apps, and sandboxes

In my first impressions post, I mentioned running into an issue with my contacts not syncing. My solution was to manually export my contacts from another phone, upload them to Google Drive, then download that file on my Pixel 3 and import the contacts into the default Contacts app on GrapheneOS.
That small, but significant hurdle became something of a pattern for my week using GrapheneOS. Throughout the week, I kept stumbling across small issues. Many could be resolved by downloading an app or tweaking the way I used the phone. Others were more challenging.
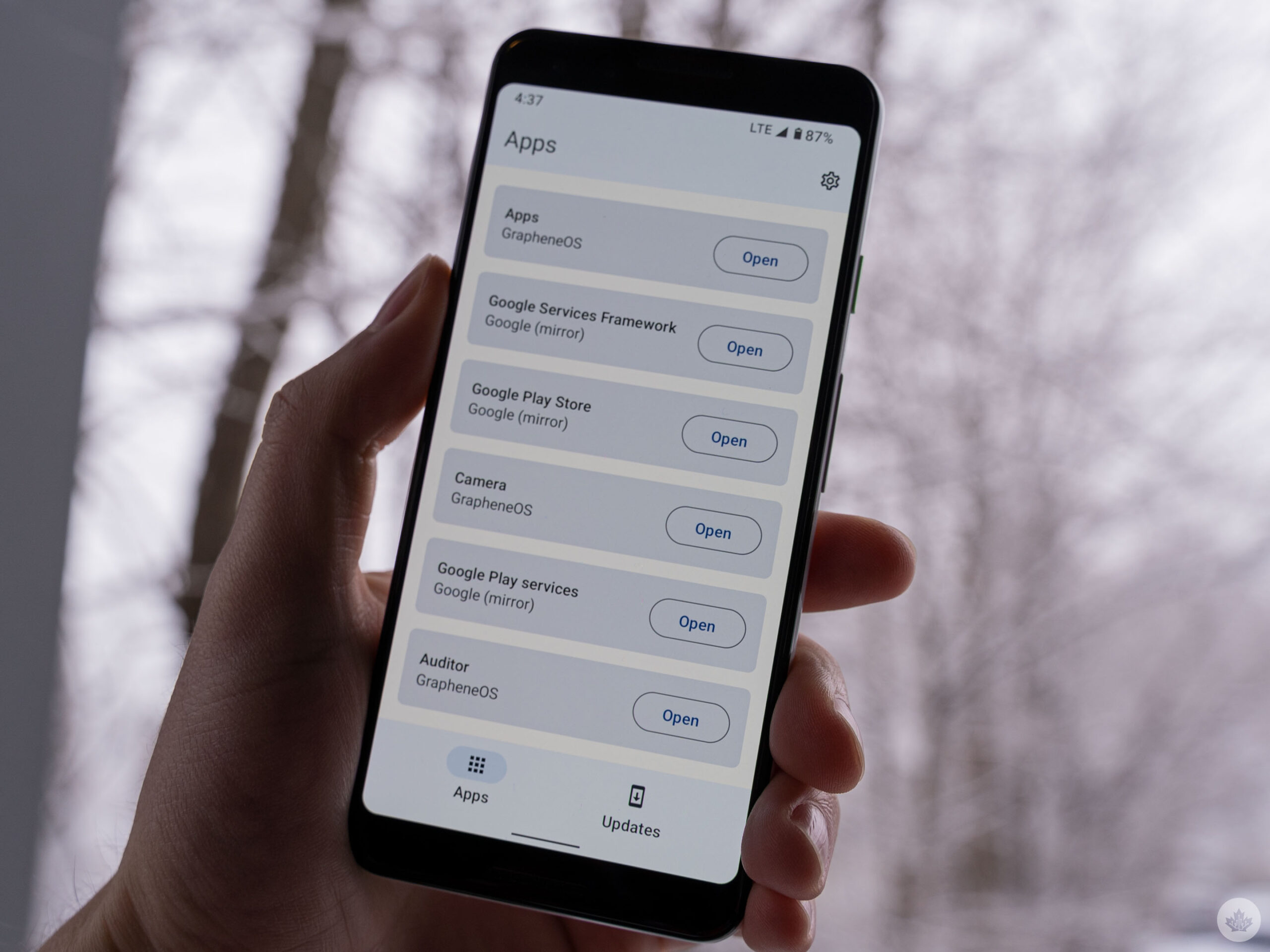
There are no Google apps installed on GrapheneOS when you first boot it up. If you want Google apps, you need to install the Play Store, Play services and the Google Services Framework from an ‘Apps’ app that comes with GrapheneOS. It’s worth noting you don’t need to install these things if you don’t want to use the Play Store, and you can use other sources for apps (for example, F-Droid or Aurora, two open-source app stores). However, some apps need the Play Store and its requisite services to power things like notifications.

The beauty of GrapheneOS is it lets you run these apps with a compatibility layer that sandboxes them (i.e. isolates them from other parts of the system) and makes the Google apps run like normal Android apps with permissions and other restrictions. In other words, those who want to run Google apps can do so while maintaining some privacy (although you are still running Google apps). Plus, you can also use GrapheneOS’ built-in profiles to, for example, divide your apps between ‘Personal’ and ‘Work’ use, adding extra layers of separation between your data.
One of the more interesting consequences of this was I had to give the Play Store permission to install apps on my phone by toggling the option to let it ‘Install unknown apps.’ I also noted seemingly improved standby battery life on the Pixel 3 with GrapheneOS. There was one day where I took the phone off the charger at 100 percent at 8am and after a day of light use, it still had 80 percent left in the tank at 4pm. Using the phone still drains the battery quickly, but the standby time impressed me.
All of this worked without a hitch in my experience, and I had no problem installing and using apps from the Play Store.
Filling a G-shaped hole

With the Play Store set up, you can also download the various Google apps, although it isn’t entirely necessary unless you expect certain things from your Android experience. For example, there’s no voice assistant on GrapheneOS. Instead, I had to download the Google Assistant and Google apps from the Play Store and change a few settings (such as setting Google as the default assistant app) before I could use Assistant like I would on an unmodified phone.
Once I made it through the hurdles, Assistant worked as well as it would on any other Android phone. It’s worth noting that fans of the ‘Hey Google’ wake word can’t use it on GrapheneOS — the feature is flat-out disabled and I couldn’t see a way to enable it. But, if you care about privacy, disabling the wake word is for the best.
Other Google apps worked fine as well once I installed them. That includes Gmail, Google Photos, Drive, Keep, and Google’s Phone and Messages app (Messages did give me some issues until I enabled some permissions for it, then it worked fine). Google Pay also appeared to be present and functional, but since I don’t use Google Pay normally I didn’t test it. On that note, banking apps might be a pain point for some (I was able to install mine, but since GrapheneOS isn’t an official Android release, it may cause problems).
Still, some of the “smart” features I’ve grown used to were still missing. For example, Google’s Phone app didn’t have Call Screen, a feature I’ve come to rely on. The keyboard also threw me for a loop — GrapheneOS includes a default keyboard that looks just like Google’s Gboard, but with worse autocorrect and missing features like swipe typing and surprisingly no emoji.
Likewise, the default camera app is functional, but it felt less intelligent than Google’s Pixel camera app.
Private OS, not so private apps

Of course, if any of these things are deal-breakers, you can work around them by installing the Google versions from the Play Store. But I found myself wondering if my privacy was actually better off for using GrapheneOS if I still frequently used Google software.
Again, you don’t have to use any of these apps or features. Gmail and Keep were the only Google apps I downloaded out of need — the others I grabbed because I wanted to test if they worked.
However, there’s a difference between getting by and flourishing — and I was just getting by with GrapheneOS. I attribute that to my over-reliance on Google apps.
Ultimately, those considering giving GrapheneOS a try need a few things to really make it work. First is a willingness to trade convenience for privacy. Like I wrote in my initial impressions, GrapheneOS works great, but I often found it lacked features I’ve come to rely on, features that make using my smartphone easier and more convenient. These are almost always tied to one Google service or another. Those who don’t care about Google’s apps or who are happy with a more basic smartphone experience will find a lot to like in GrapheneOS.
Basic troubleshooting skills are also a must to make the most out of the mobile OS. It’s not a matter of if, but when you’ll run into a problem. It could be a small hiccup like not having emojis or something more drastic like an app not working because you’re missing some integral Google software it relies on.

I never had to get technical to solve these problems, but I did have to think outside the box. The issue with my contacts is a prime example — instead of relying on Google’s broken sync software, I manually transferred my contacts through Google Drive. It wasn’t difficult, but not everyone would think to try something like that.
Overall, I really liked GrapheneOS, but it was generally incompatible with how I use my phone (and with my job, which generally revolves around writing about the latest tech features). I think I could run GrapheneOS as my daily driver and be perfectly happy in a world where my smartphone wasn’t such an integral part of both my career and my life. I’ll be keeping an eye on GrapheneOS going forward, but my SIM is going back to the Pixel 6 for now.