Following Apple’s announcement that it will sue NSO for attacking iOS users, the iPhone-maker also revealed its monitoring devices for signs of compromise and will alert users with affected devices.
As a refresher, NSO is an Israel-based company that developed the ‘Pegasus‘ spyware used to compromise iPhones. NSO claims it only sells the tool to governments and law enforcement agencies, but reports show that Pegasus was used against activists, journalists and even Jeff Bezos (just to name a few targets).
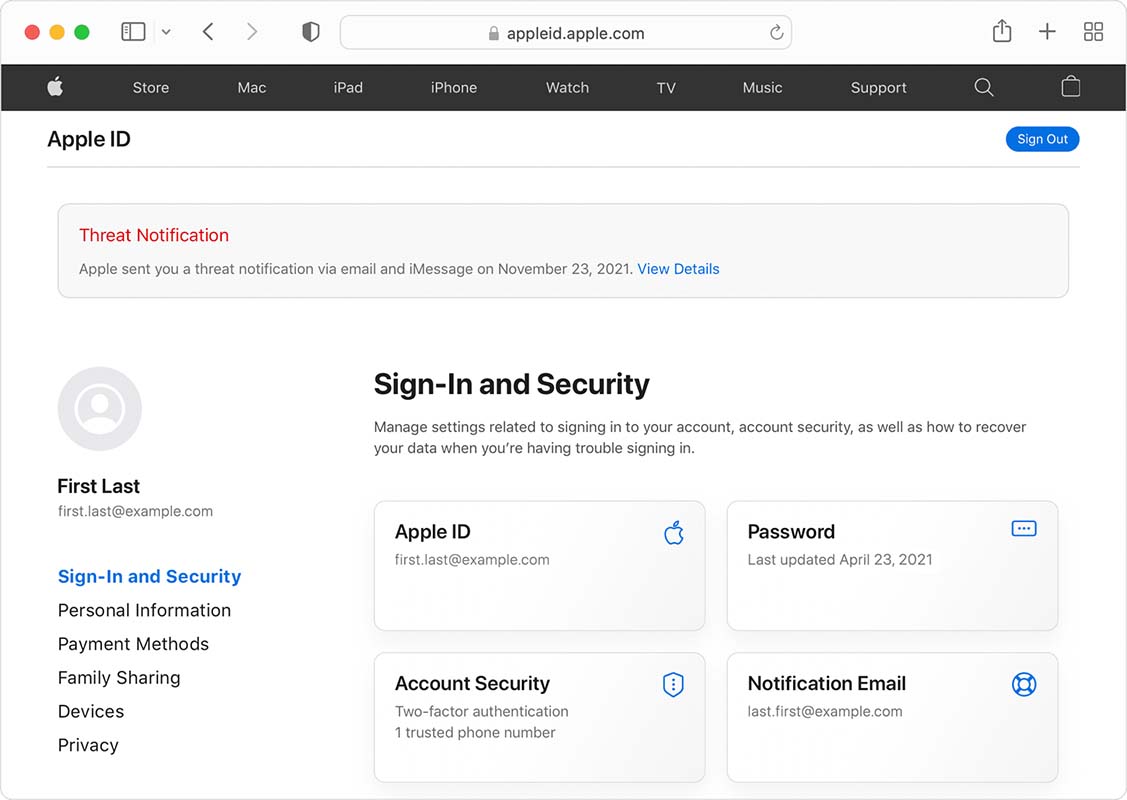
According to a new support document from Apple, the company will deliver threat notifications to people potentially targeted by Pegasus in three ways: via iMessage, email and an alert on the Apple ID website (pictured below).
Further, Apple says that these threat notifications will never ask users to click on any links or install anything. If you receive a threat notification and aren’t sure about its validity, Apple suggests you sign into ‘appleid.apple.com’ to check.
However, the company also acknowledges that things can change quickly, and says it cannot guarantee it will detect all attacks. Apple warns that false alarms are possible as well.
Finally, Apple lays out several steps iPhone owners should take to further protect themselves from potential attacks. Steps include updating devices to the latest software and security fices, protecting devices with a passcode, using two-factor authentication (2FA) and a strong password for their Apple ID, only installing apps from the App Store (where else would you get them?), using strong passwords for online services and finally, Apple warns not to click on links or attachments from unknown senders.
That last one is particularly important when it comes to Pegasus. One of the main ways attackers deliver spyware is by sending links or files to targets. When clicked, these links or files can install Pegasus without the target’s knowledge.
It might also be wise to avoid clicking links or files sent by people in your contacts too. It’s entirely possible for attackers to spoof sender details to make it look like something’s coming from a familiar source.
All that said, most people probably don’t need to worry about Pegasus on their phones. The tool is often deployed against journalists, activists, politicians and other public or important figures, not average people. Still, at least now there’s some reassurance that if an attacker used Pegasus against you, Apple might be able to warn you about it.
Those interested can learn more about Apple’s threat notifications here.
Source: Apple Via: 9to5Mac










